SIEM is implemented via software, systems, appliances, or some combination of these items. There are, generally speaking, six main attributes of an SIEM system:
Retention: Storing data for long periods so that decisions can be made off of more complete data sets.
Dashboards: Used to analyze (and visualize) data in an attempt to recognize patterns or target activity or data that does not fit into a normal pattern.
Correlation: Sorts data into packets that are meaningful, similar and share common traits. The goal is to turn data into useful information.
Alerting: When data is gathered or identified that trigger certain responses – such as alerts or potential security problems – SIEM tools can activate certain protocols to alert users, like notifications sent to the dashboard, an automated email or text message.
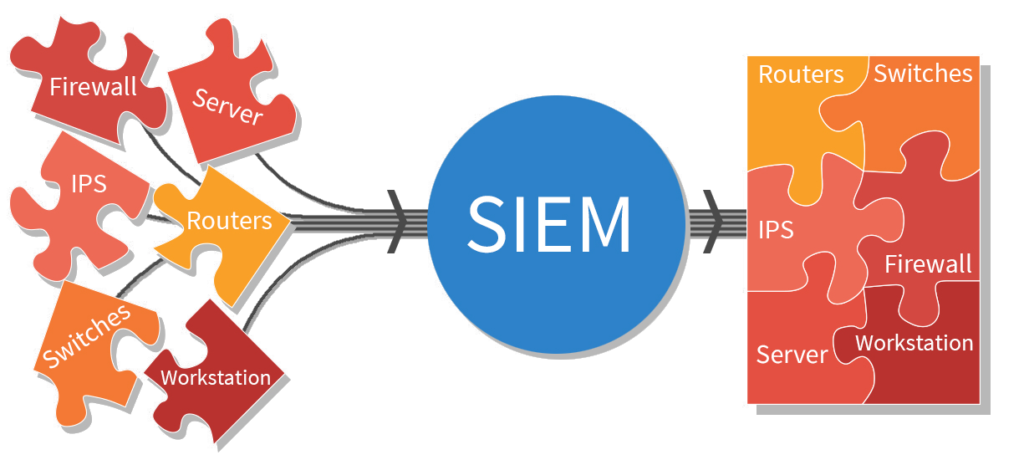
Data Aggregation: Data can be gathered from any number of sites once SIEM is introduced, including servers, networks, databases, software and email systems. The aggregator also serves as a consolidating resource before data is sent to be correlated or retained.
Compliance: Protocols in a SIEM can be established that automatically collect data necessary for compliance with company, organizational or government policies.
 |  |
 |
